2024_ISCTF_Pwn 小蓝鲨的stack 出题人:安阳工学院_笙南
解题过程:
⽐较少⻅的⼀个题型,不过并不难,
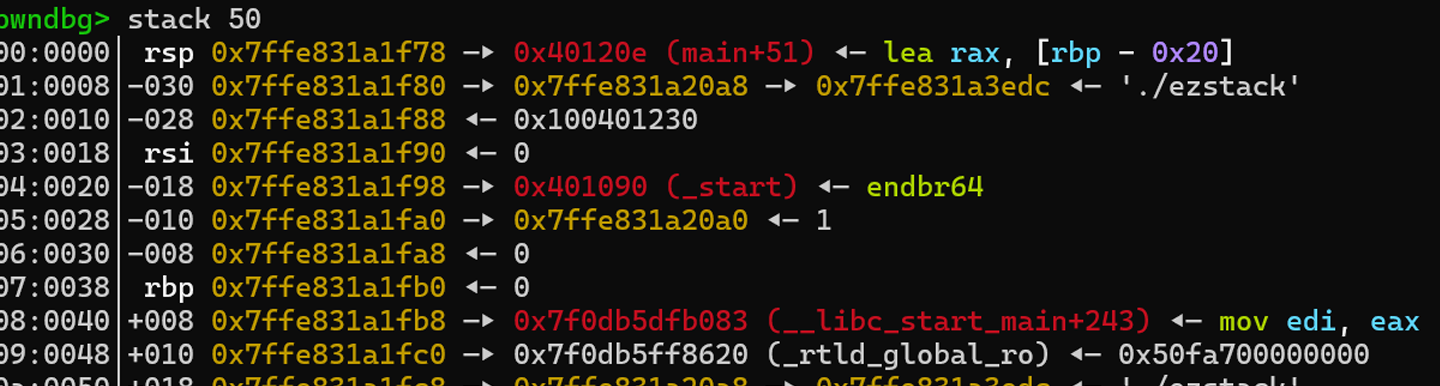
ida64查看代码发现只有⼀个read和printf打印我们输⼊的东西 这⾥是没办法通过rop链去泄露libc地址的。
程序原设定的返回地址是
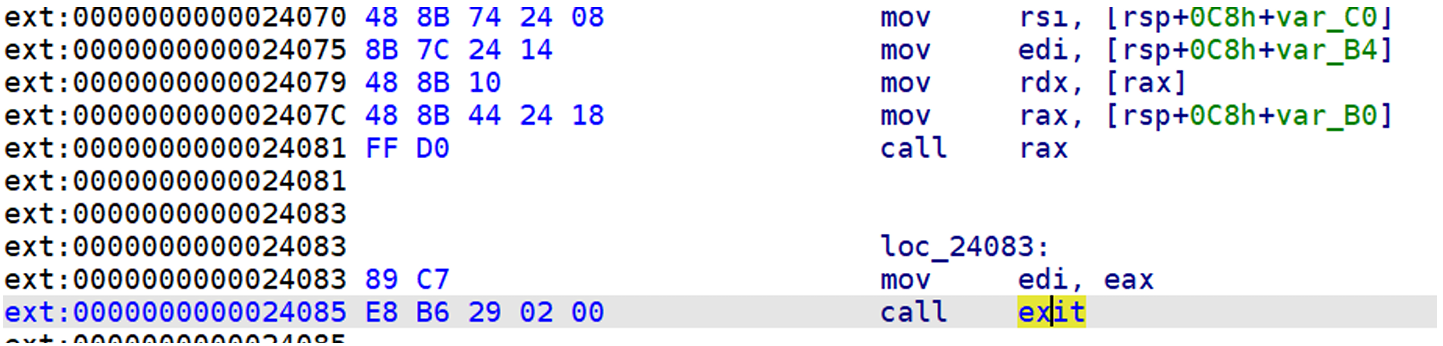
⽽我们需要利⽤的正是__libc_start_main⾥⾯的⼀段gadget 我们将libc⽂件拖⼊ida,分析__libc_start_main段上的汇编
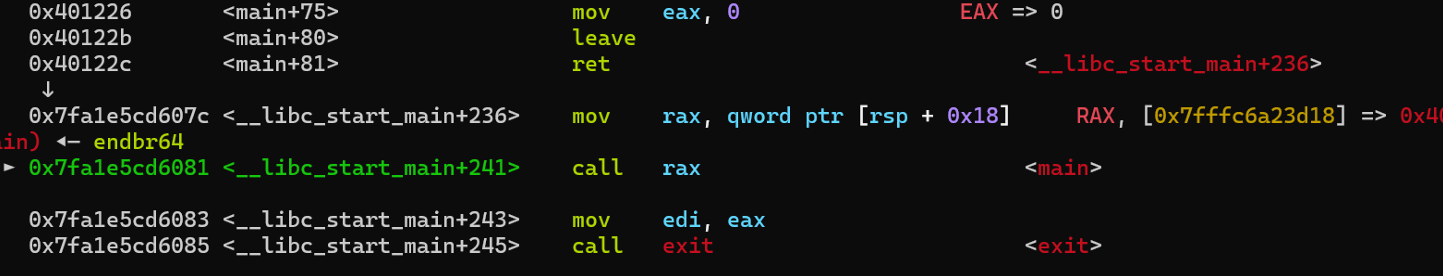
程序原返回地址是24083这⾥,我们发现在该地址上⾯还有⼀段call rax,⽽此时rax恰好被赋值为了main函数起始地址,也就是说 我们将返回地址修改为mov rax这⾥就可以再次返回到main函数,并且由于printf函数会打印我们输⼊的东西,我们还可以把返回地 址给打印出来,这样我们就拿到了libc地址,以及第⼆次利⽤read函数,接下来就是直接打rop链获得权限。
调试之后发现确实会回到main函数
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 from pwn import*
Orange 出题⼈:SunD1y
解题过程:
菜单题,edit可以溢出,⽆free,使⽤houseoforange 构造largebinattack攻击,接着使⽤edit溢出泄漏heap和libc地址触发 largebin attack,布置好fakeIOFILE之后调⽤exit触发getshell
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 #!/usr/bin/env python
netcat 出题⼈:b55t4ck
解题过程:
通过nc⼯具连接即可获得flag,linux系统⼀般⾃带nc,Windows可能需要安装nc.exe
girlfriend 出题⼈:b55t4ck
解题过程:
从IDA里面分析就是,s1越界读取,覆盖为admin,然后进入vuln中,观察到存在数组溢出,通过数组溢出就可以修改溢出长度至ret_addr的位置,随后就可以跳转到后门函数
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 from pwn import *
ret2orw 出题⼈:b55t4ck
解题思路:
给了后门函数,但是跳转后会出现bad syscall的报错,在init函数中可以看到禁用了system调用。既然可以栈溢出,那么我们就可以利⽤gadget去调⽤libc⾥⾯存在的open,read,write。从⽽读取flag。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 from pwn import *
0verf10w 出题⼈:b55t4ck
⼀道⽐较综合的题⽬,考察栈迁移,格式化字符串,还有防御机制绕过的漏洞,⾸先可以通过格式化字符串泄露canary,和libc。 再通过vuln函数溢出的⼀个字节实现栈迁移,从⽽劫持程序执⾏流,然后再通过one_gadget即可获取shell。需要注意的是,本地环 境需保持与远程⼀致,不然可能出现本地打得通远程打不通的情况。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 from pwn import *
ez_game 出题⼈:Qjzhalx
解题过程
利用gets覆盖掉seeds
1 2 3 4 5 6 7 8 9 10 11 12 13 from pwn import *